I am going to show you the easy steps to install Let’s Encrypt SSL Certificate for your Server Hostname/FQDN on your CentOS Web Panel dashboard.
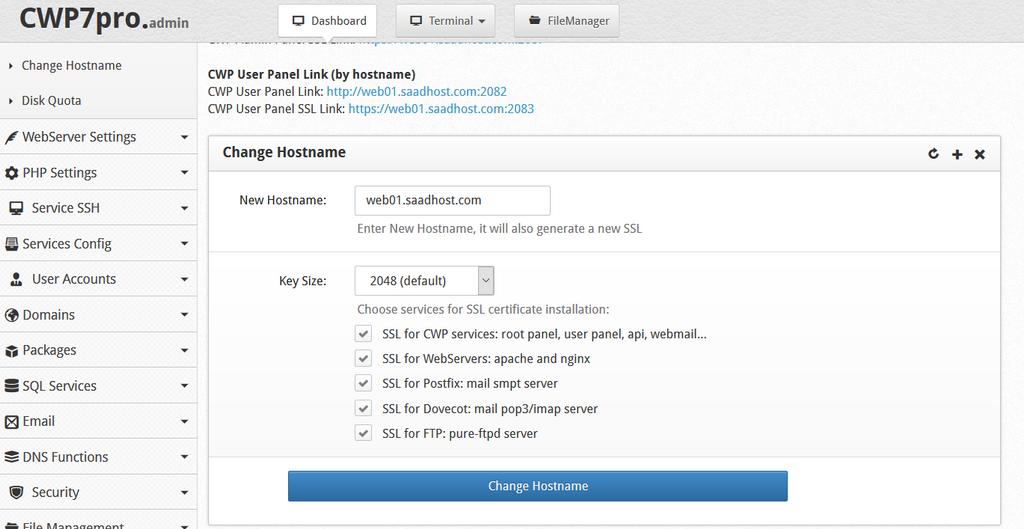
Go to Server Settings > Change Hostname in the left menu of the cwp.admin
- Enter the hostname
- Set key size (2048 or 4096)
- Choose services for SSL certificate installation
- Save by pressing the Change Hostname button
This will also generate a new free auto-SSL certificate and get it installed (if you have a valid and working A record set for it.
If you need to manually change the certificate, you can simply edit this files hostname.cert and hostname.key
2028 or 4096 Key Size?
You’re probably already aware that with a 4096 bit key:
- There’s an increase in encryption strength.
- The SSL handshake at the start of each connection will be slower.
- There’s an increase in CPU usage during handshakes.
Algos like RSA (unfortunately) don’t double in strength when you add a single bit.
2048 bit RSA key has a strength of 112 bits: i.e., there are theoretically 2112 possibilities to crack the private key.
| Security Strength | RSA key length |
| <= 80 | 1024 |
| 112 | 2048 |
| 128 | 3072 |
| 192 | 7680 |
| 256 | 15360 |
Measuring the increased load on the server
Bigger RSA key sizes may slow down handshaking from the users point of view. On a Mac or Linux machine you can get some time taken to sign a 2048 bit RSA vs 4096 bit RSA with the openssl speed rsa command:
sign verify sign/s verify/s
rsa 512 bits 0.000210s 0.000014s 4772.1 69667.5
rsa 1024 bits 0.000727s 0.000035s 1375.3 28508.9
rsa 2048 bits 0.003778s 0.000092s 264.7 10899.5
rsa 4096 bits 0.022637s 0.000305s 44.2 3275.4Looking at the results, it’s pretty clear:
4096 bit handshakes are indeed significantly slower in terms of CPU usage than 2048 bit handshakes.
But secure file transfer protocols like HTTPS, FTPS, or SFTP normally use RSA keys only during the start of the connection, when they’re used in encrypting the symmetric keys. Once you start transmitting the data, it’s going to be the symmetric keys that are going to be used in the subsequent encryption processes.
So, the performance hit due to a 4096-bit key will only be felt within a small fraction of the entire file transfer session. Of course, if your server carries out a large number of concurrent file transfers, then the performance hits can add up.
Acceptability
| Security Strength | Through 2030 | 2031 and beyond |
| < 112 | Disallowed | Disallowed |
| 112 | Acceptable | Disallowed |
| 128 | Acceptable | Acceptable |
| 192 | Acceptable | Acceptable |
| 256 | Acceptable | Acceptable |